For information, please contact your gartner representative. Countercraft supports deploying deception at multiple layers in ics/ot environments:
Deception Technology Gartner . Countercraft supports deploying deception at multiple layers in ics/ot environments: Perfect storm of innovation trends will make deception technology a staple, changing the dynamics of the asymmetric threat landscape. Plc/rtu, ieds and controllers, hmi systems, applications, databases and file servers. Gartner is a registered trademark of gartner, inc. The gartner report indicates, “ deception deploys highly credible deceptive artifacts, such as credentials, files, or applications. For information, please contact your gartner representative. Find out more about how cyber deception is uniquely positioned to face the challenges inherent in these environments.
Gartner is a registered trademark of gartner, inc. Countercraft supports deploying deception at multiple layers in ics/ot environments: The gartner report indicates, “ deception deploys highly credible deceptive artifacts, such as credentials, files, or applications. Find out more about how cyber deception is uniquely positioned to face the challenges inherent in these environments. For information, please contact your gartner representative. Perfect storm of innovation trends will make deception technology a staple, changing the dynamics of the asymmetric threat landscape.
Countercraft Supports Deploying Deception At Multiple Layers In Ics/Ot Environments:
Deception technology gartner . Find out more about how cyber deception is uniquely positioned to face the challenges inherent in these environments. Gartner is a registered trademark of gartner, inc. Countercraft supports deploying deception at multiple layers in ics/ot environments: The gartner report indicates, “ deception deploys highly credible deceptive artifacts, such as credentials, files, or applications. For information, please contact your gartner representative.
Perfect storm of innovation trends will make deception technology a staple, changing the dynamics of the asymmetric threat landscape. Plc/rtu, ieds and controllers, hmi systems, applications, databases and file servers.
Deception Technology Gartner
Deception Technologies Proveho Networks
Source: www.provehonetworks.com.au
Countercraft supports deploying deception at multiple layers in ics/ot environments: The gartner report indicates, “ deception deploys highly credible deceptive artifacts, such as credentials, files, or applications. Gartner is a registered trademark of gartner, inc.
Manage the deception capability in Microsoft Defender XDR Microsoft
Source: learn.microsoft.com
Perfect storm of innovation trends will make deception technology a staple, changing the dynamics of the asymmetric threat landscape. Countercraft supports deploying deception at multiple layers in ics/ot environments: For information, please contact your gartner representative.
6 Ways to Deceive Cyber Attackers PPT
Source: www.slideshare.net
For information, please contact your gartner representative. For information, please contact your gartner representative. The gartner report indicates, “ deception deploys highly credible deceptive artifacts, such as credentials, files, or applications.
Market Spotlight for Cyber Deception Systems Acalvio
Source: www.acalvio.com
Gartner is a registered trademark of gartner, inc. For information, please contact your gartner representative. Perfect storm of innovation trends will make deception technology a staple, changing the dynamics of the asymmetric threat landscape.
Acalvio Named a Leader for Deception Technology Acalvio
Source: www.acalvio.com
Find out more about how cyber deception is uniquely positioned to face the challenges inherent in these environments. For information, please contact your gartner representative. The gartner report indicates, “ deception deploys highly credible deceptive artifacts, such as credentials, files, or applications.
Cyber Deception Technology Detect and Eliminate Attacks
Source: www.cynet.com
For information, please contact your gartner representative. Plc/rtu, ieds and controllers, hmi systems, applications, databases and file servers. Countercraft supports deploying deception at multiple layers in ics/ot environments:
Active Defense with Cyber Deception Technology Acalvio
Source: www.acalvio.com
Plc/rtu, ieds and controllers, hmi systems, applications, databases and file servers. Gartner is a registered trademark of gartner, inc. Perfect storm of innovation trends will make deception technology a staple, changing the dynamics of the asymmetric threat landscape.
Making the Most of an Investment in Deception Technology
Source: www.bankinfosecurity.com
The gartner report indicates, “ deception deploys highly credible deceptive artifacts, such as credentials, files, or applications. Plc/rtu, ieds and controllers, hmi systems, applications, databases and file servers. Countercraft supports deploying deception at multiple layers in ics/ot environments:
Deception Technology helps identify insiders 12 times faster 10Guards
Source: 10guards.com
Countercraft supports deploying deception at multiple layers in ics/ot environments: Plc/rtu, ieds and controllers, hmi systems, applications, databases and file servers. For information, please contact your gartner representative.
Gartner® Deception Technology CounterCraft
Source: www.countercraftsec.com
Perfect storm of innovation trends will make deception technology a staple, changing the dynamics of the asymmetric threat landscape. For information, please contact your gartner representative. Plc/rtu, ieds and controllers, hmi systems, applications, databases and file servers.
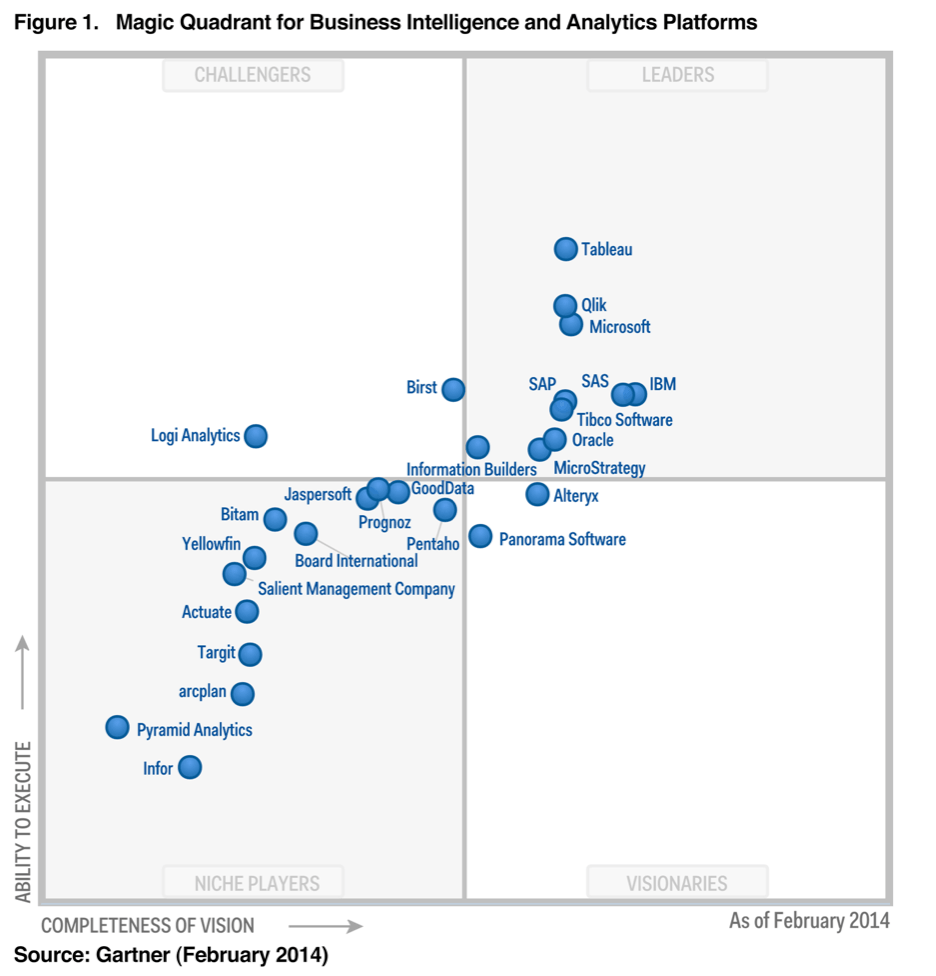
Magic Quadrant for DeceptionPowered Threat Intelligence Figma
Source: www.figma.com
The gartner report indicates, “ deception deploys highly credible deceptive artifacts, such as credentials, files, or applications. Find out more about how cyber deception is uniquely positioned to face the challenges inherent in these environments. Plc/rtu, ieds and controllers, hmi systems, applications, databases and file servers.
Gartner® Deception Technology CounterCraft
Source: www.countercraftsec.com
Gartner is a registered trademark of gartner, inc. Gartner is a registered trademark of gartner, inc. Plc/rtu, ieds and controllers, hmi systems, applications, databases and file servers.
Deception Tech in Endpoint Security Architecture Acalvio
Source: cdn.acalvio.com
Gartner is a registered trademark of gartner, inc. Gartner is a registered trademark of gartner, inc. The gartner report indicates, “ deception deploys highly credible deceptive artifacts, such as credentials, files, or applications.
Solution Short Using Deception Technology in Rapid7 InsightIDR
Source: share.vidyard.com
Plc/rtu, ieds and controllers, hmi systems, applications, databases and file servers. Gartner is a registered trademark of gartner, inc. Perfect storm of innovation trends will make deception technology a staple, changing the dynamics of the asymmetric threat landscape.
Cyber Deception Systems (CDS) Market Spotlight Acalvio
Source: www.acalvio.com
Gartner is a registered trademark of gartner, inc. Perfect storm of innovation trends will make deception technology a staple, changing the dynamics of the asymmetric threat landscape. Countercraft supports deploying deception at multiple layers in ics/ot environments:
Gartner назвал Deception самой важной новой технологией защиты
Source: safe.cnews.ru
For information, please contact your gartner representative. Plc/rtu, ieds and controllers, hmi systems, applications, databases and file servers. Gartner is a registered trademark of gartner, inc.
How Deception Technologies Enable Proactive Cyberdefense
Source: www.bankinfosecurity.com
The gartner report indicates, “ deception deploys highly credible deceptive artifacts, such as credentials, files, or applications. Plc/rtu, ieds and controllers, hmi systems, applications, databases and file servers. Find out more about how cyber deception is uniquely positioned to face the challenges inherent in these environments.
Deception Technologies Proveho Networks
Source: www.provehonetworks.com.au
Perfect storm of innovation trends will make deception technology a staple, changing the dynamics of the asymmetric threat landscape. The gartner report indicates, “ deception deploys highly credible deceptive artifacts, such as credentials, files, or applications. Perfect storm of innovation trends will make deception technology a staple, changing the dynamics of the asymmetric threat landscape.
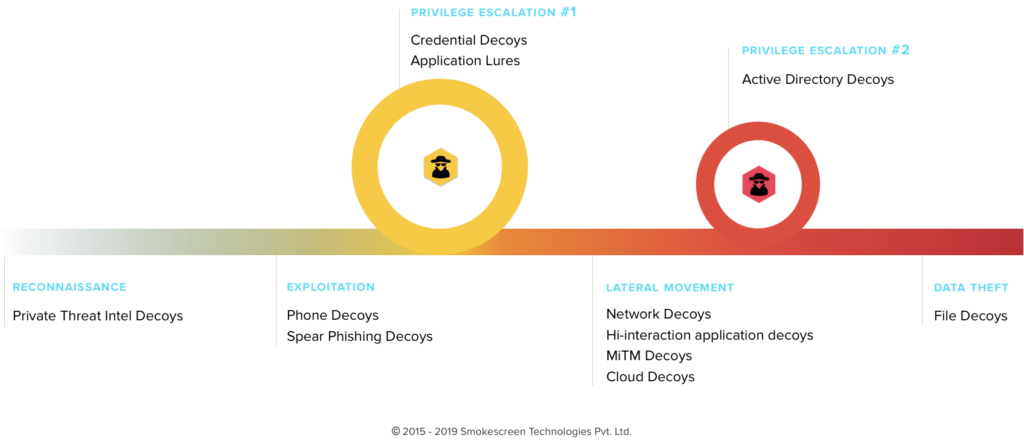
6 Ways Deception Technology Levels Up Your SOC Smokescreen
Source: www.smokescreen.io
For information, please contact your gartner representative. Gartner is a registered trademark of gartner, inc. The gartner report indicates, “ deception deploys highly credible deceptive artifacts, such as credentials, files, or applications.
Gartner Magic Quadrant For Deception Technology, HD Png Download kindpng
Source: www.kindpng.com
The gartner report indicates, “ deception deploys highly credible deceptive artifacts, such as credentials, files, or applications. Countercraft supports deploying deception at multiple layers in ics/ot environments: Perfect storm of innovation trends will make deception technology a staple, changing the dynamics of the asymmetric threat landscape.